This blog post was written in order to explain the functionality of the critical vulnerability CVE-2014-6324 found in the Windows implementation of the Kerberos authentication protocol. This bug allows an attacker to elevate unprivileged domain user privileges to a Domain Administrator account. Microsoft recently issued the patch MS14-068 which fixes this critical security vulnerability.
Vulnerability ExplainedIn order to understand the vulnerability it is required to have an understanding of how Kerberos works. Kerberos is a network authentication protocol used to provide secure access across potentially hostile networks. The protocol uses a "Ticket" exchanging mechanism, for both the client and server to prove their identity to access the network services. The first part is handled by the LSASS.exe process. When the user logs in with his credentials (request) through Winlogon, the LSA (Local Security Authority) processes them and passes them to Kerberos.dll in an encrypted format. Afterwards, the whole process is guided by the DC\KDC (also known as Kerberos Key Distribution Center). Two other services, namely the AS (Authentication Service) and the TGS (Ticket Granting Service) which are running in the KDC, also play a vital role.
Ticket Exchange Mechanism of Kerberos
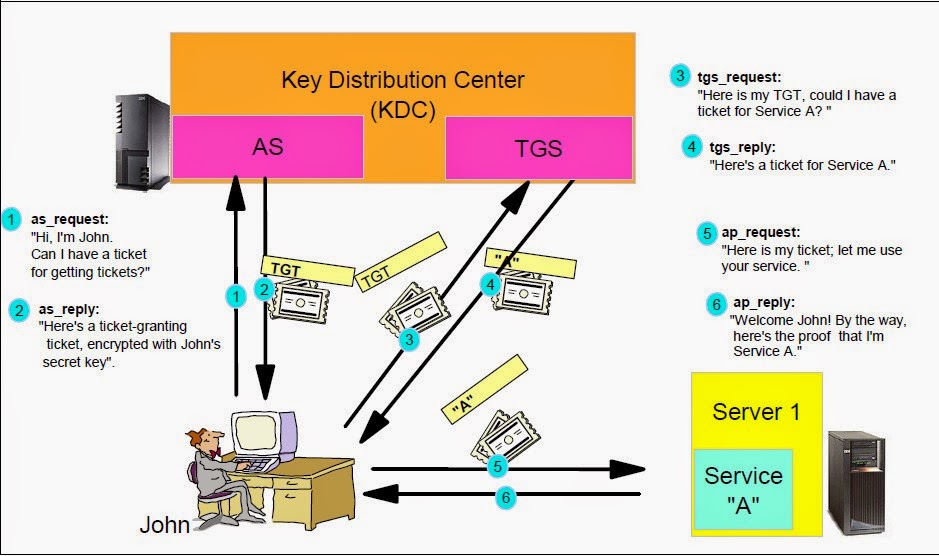
Figure (a)
In the image above the KDC replies to both requests (as_request and tgs_request) with the TGT (Ticket to Get Tickets). The TGT contains a blob of data which is known as the PAC (Privilege Attribute Certificate). The PAC contains among other things the user's domain SID, as well as the security groups that the user is a member of.
PAC in Kerberos Protocol Extension
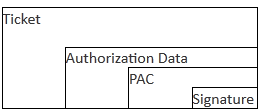
Figure (b)
Figure (b) shows the simplified structure of the PAC. As can be seen, the PAC stores an additional signature which is later verified by the TGS.
With the reference to the above Figure (a) when a user first sends the as_request message to the Authentication Service, it sends back the first TGT containing the PAC blob which stores the user's security information. It also signs the PAC and stores the signature as shown in the Figure (b), so that the PAC can't be tampered with by an attacker. The user then sends the tgs_request message for the service ticket to the Ticket Granting Service in order to access the particular service, as shown in the image above (it's requesting a service ticket for service A). The user can only send the request to the TGS when it gets authenticated from the AS and it is in posession of the TGT. Before providing the service ticket, the TGS validates the signature of the PAC contained in the TGT and if a valid signature is found, it copies the PAC into the Service Ticket being created.
Now when the user authenticates to the service using that Service Ticket issued by the TGS it once again validates the signature of the PAC and the data inside the PAC blob which stores the user information to create the logon tokens for the user. As an example, if the PAC has a valid signatures and is stating that user John belongs to the group of Domain Administrators, a valid login token is created and John will be a member of the Domain Administrators from now on.
CVE-2014-6324 affects the way Windows Kerberos validates the PAC signature. By exploiting the vulnerability an authenticated domain user could send a forged Kerberos ticket to the Kerberos KDC that claims that the user is a member of any group such as the Domain Administrators. The Kerberos KDC would improperly validate the forged ticket signature when processing the request from the attacker, allowing the attacker to access any resource on the network with the identity of a Domain Administrator.
Systems Affected by CVE-2014-6324:Domain controllers running Windows Server 2008-R2 and below are affected by this vulnerability. After more tests it has been confirmed that this vulnerabililty also exists on Windows Server 2012 and higher, but exploiting it on Window Server 2012 and newer versions is deemed to be more difficult. In general this vulnerbility is affecting almost all the Microsoft operating systems.
Out-of-band Patch MS-014-068:The patch MS14-068 was released by Microsoft on November 18, 2014 as an out-of-band patch. This patch fixes the way the KDC is performing the signature verification for the PAC signature. The functions inside kdsvc.dll which are performing the signature validation now don't allow any valid signature algorithm to be used for the PAC signature but restrict the signature type to a known good value. If the signature type does not match the HMAC_MD5 algorithm, an error is returned and the signature will not be verified successfully.
So if you haven't download the latest Microsoft patches, hurry up!

